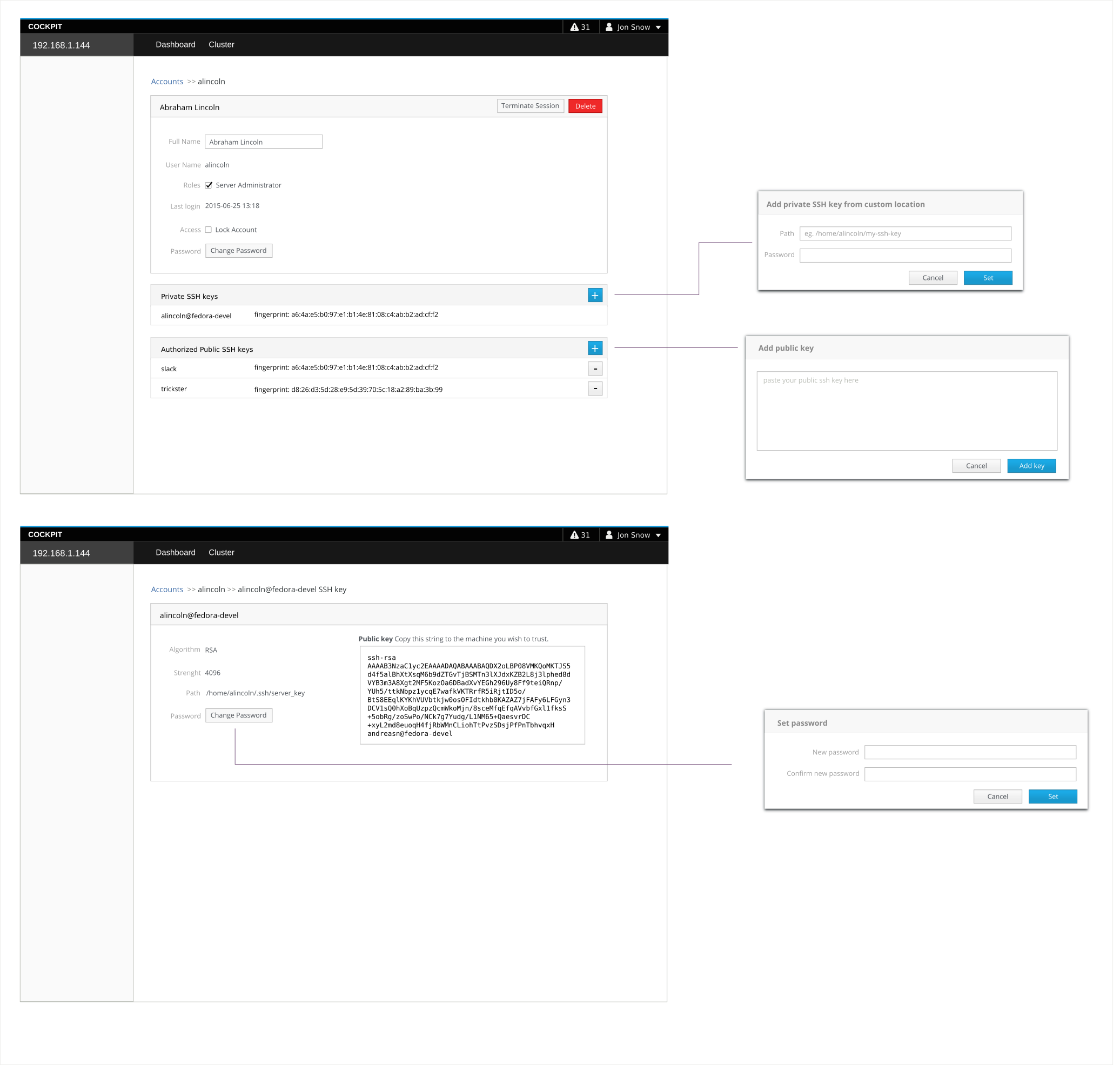
Feature: Key based authentication
Many deployments only support ssh via key based authentication. Cockpit should allow users to connect to remote machines via ssh using key based authentication.
Phillip J. Fry leads a small IT at a moderately sized firm. His company runs their applications on a few virtual machines in the public cloud. Password based authentication is not permitted. SSH access is granted to those machines by adding his public key to his account with the providers API.
Robert Paulson is a developer at a small IT company. For one reason or another, he got tossed the sysadmin hat at the company. One of their cloud servers is running the company's website. Robert uses key based authentication to access the server when he's working from home. Yesterday was somewhat a shitty day for Robert, since his car was broken into while his personal laptop was in the car. That laptop had a copy of the ssh key that can authenticate against the company's server. The thief probably only want to wipe the disk and sell the laptop on, but you never know...
Phillip:
- Connects to cockpit running on his local machine.
- Philip is able to connect to and add his cloud machines to his cockpit dashboard.
Robert:
- Logs in to cockpit using his work laptop.
- He removes the ssh key associated with the stolen laptop.
[
- In the past there was some discussion of being able to log into a machine other than localhost. Do we want work that in here.
- Yes, any machine could be used as a bastion. But i didn't really want to get into describing best practices for setting that up.