The Cyber Security Body of Knowledge (CyBOK) is a body of knowledge that aims to encapsulate the various knowledge areas present within cyber security. Scenarios within SecGen now contain XML elements linking them to CyBOK knowledge areas and specific topics within those knowledge areas. Additionally, video lectures for scenarios are tagged with their CyBOK associations.
This file is an autogenerated index of the lecture videos referenced by scenarios -- with CyBOK metadata.
There are 71 videos with CyBOK metadata.
Cyber Security Body of Knowledge (CyBOK) Issue 1.1 is Crown Copyright, The National Cyber Security Centre 2021, licensed under the Open Government Licence http://www.nationalarchives.gov.uk/doc/open-government-licence/.
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=sv1pHuuoW9g
| KA | Topics | Keywords |
|---|---|---|
| (IC) | Foundational Concepts | objectives of cyber security |
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=grISRv-CuHE
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; Protecting integrity |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Linux read only protections: ro mounts; file attributes |
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=qzyEdeQ_7ZY
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Artifact Analysis | cryptographic hashing |
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | MONITORING - FILE INTEGRITY CHECKERS |
| Operating Systems & Virtualisation (OSV) | OS Hardening | code and data integrity checks |
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=kz7m-iyzSOw
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | Fundamental Concepts | workflows and vocabulary; architectural principles |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; handle: actual incident response; follow up: post incident activities; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE; incident response methodologies |
| Law & Regulation (LR) | Data Protection | investigation and prevention of crime; personal data breach notification; enforcement and penalties |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | Recover data and services after an incident |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | Recover data and services after an incident; BACKUP - DIFFERENTIAL; BACKUP - INFERENTIAL |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | DATA REDUNDANCY; REDUNDANCY IN NETWORK SERVICES |
| Distributed Systems Security (DSS) | CLOUD - COMPUTING - SERVICES | CLOUD COMPUTING - DEPLOYMENT MODELS; CLOUD COMPUTING - RESOURCE POOLING; CLOUD COMPUTING - SERVICE MODELS - IAAS; CLOUD COMPUTING - SERVICE MODELS - PAAS; CLOUD COMPUTING - SERVICE MODELS - SAAS; CLOUD COMPUTING - STORAGE |
| Operating Systems & Virtualisation (OSV) | CLOUD - COMPUTING - SERVICES | CLOUD COMPUTING - VIRTUALIZATION |
| Privacy & Online Rights (POR) | Confidentiality | CLOUD COMPUTING - PRIVACY CONCERNS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | DATA REDUNDANCY |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | the base-rate fallacy |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | intrusion detection systems |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
by Z. Cliffe Schreuders
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections; artifacts and fragments; challenges of live forensics |
| Operating Systems & Virtualisation (OSV) | OS Hardening | anomaly detection |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=iUInvMrBw3k
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections; artifacts and fragments; challenges of live forensics |
| Operating Systems & Virtualisation (OSV) | OS Hardening | anomaly detection |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Operating System Analysis | storage forensics; data recovery and file content carving; Timeline analysis |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Fundamental Concepts | workflows and vocabulary; PURPOSE OF LOGGING AND AUDITING |
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | system and kernel logs; Syslog; Linux Journal and SystemD; EVENTS - LOGGING; LOG FILES - CENTRALIZED LOGGING; LOG FILES - EVENT SOURCE CONFIGURATION; Log format: Common Log Format (CLF) |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | contribution of SIEM to analysis and detection |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Taxonomy | potentially unwanted programs |
| Operating Systems & Virtualisation (OSV) | Attacker Model | attack surface; threats to security for modern OSs |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Taxonomy | dimensions; kinds; potentially unwanted programs |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Detection | ANTI-MALWARE - SYSTEMS; ANTIVIRUS SOFTWARE; MALCODE/MALWARE - COUNTERMEASURES - CODE SIGNING; MALCODE/MALWARE - COUNTERMEASURES - SANDBOXING; MALCODE/MALWARE - THIRD-PARTY CERTIFICATIONS |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: C |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: C |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: ASM; Technical underpinnings for malware analysis: C |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Attacks and exploitation | EXPLOITATION |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Attacks and exploitation | EXPLOITATION |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | structured output generation vulnerabilities |
| Software Security (SS) | Prevention of Vulnerabilities | structured output generations mitigations |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | race condition vulnerabilities |
| Software Security (SS) | Prevention of Vulnerabilities | race condition mitigations |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | Format string attacks |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Detection of Vulnerabilities | dynamic detection |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Detection of Vulnerabilities | dynamic detection |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
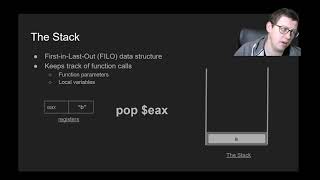
| Software Security (SS) | Technical Underpinning | Technical underpinnings for memory management vulnerabilities: the stack |
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Technical Underpinning | Technical underpinnings for memory management vulnerabilities: the stack |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Prescriptive Processes | Microsoft SDL |
| Risk Management & Governance (RMG) | THREAT ANALYSIS | THREAT MODEL; ATTACK TREES |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Prescriptive Processes | Microsoft SDL |
| Risk Management & Governance (RMG) | THREAT ANALYSIS | THREAT MODEL; ATTACK TREES |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | OS Security Principles | Saltzer and Schroeder’s principles; newer principles |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Motivations for Secure Software Lifecycle | vulnerabilities can be exploited without being noticed |
| (SSL) | Prescriptive Processes | Microsoft SDL; SAFECode; Touchpoints |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
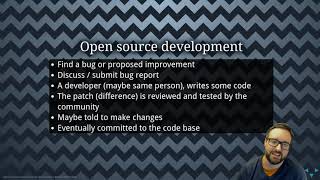
| (SSL) | Prescriptive Processes | Open source secure development |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication; Types of user accounts |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
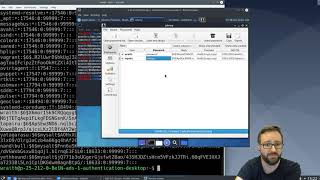
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication; AUTHENTICATION - BIOMETRICS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication; AUTHENTICATION - OTP (ONE-TIME PASSWORD); AUTHENTICATION - TOKENS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHORIZATION - SSO (SINGLE SIGN-ON); AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL); AUTHENTICATION - KERBEROS; ACTIVE DIRECTORY DOMAIN SERVICES (ADDS) |
| Authentication, Authorisation & Accountability (AAA) | Access Control in Distributed Systems | core concepts; federated access control |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | theory; Network based-authentication with heterogeneous Linux and Windows networks; AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL) |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHENTICATION - KERBEROS |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHORIZATION - SSO (SINGLE SIGN-ON); AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL); AUTHENTICATION - KERBEROS; ACTIVE DIRECTORY DOMAIN SERVICES (ADDS) |
| Authentication, Authorisation & Accountability (AAA) | Access Control in Distributed Systems | core concepts; federated access control |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; enforcing access control; theory |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | mediation; TRUSTED COMPUTING BASE (TCB); REFERENCE MONITOR |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; enforcing access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; filesystems; inodes; and commands |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | mediation |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; theory; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL); ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL); ACCESS CONTROL - ROLE-BASED |
| Operating Systems & Virtualisation (OSV) | OS Security Principles | security models |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; Elevated privileges; Real and effective identity; Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; setuid/setgid |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; ACCESS CONTROL - MATRIX; ACCESS CONTROL LIST (ACL); Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | capabilities |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; ACCESS CONTROL LIST (ACL); Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Linux Extended Access Control Lists (facl) |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | SANDBOX; Application-based access controls: user-based access controls insufficiently limit privileges |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | capabilities; Container-based sandboxes: chroot; Docker; Rule-based controls: Course grained: Linux capabilities; System-level sandboxes (complete OS; Qubes); hardware-emulation and paravirtualisation; Copy on write sandboxes |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | isolation; CONTAINERS |
| Web & Mobile Security (WAM) | Fundamental Concepts and Approaches | sandboxing; permission dialog based access control |
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL); ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL); Application-based access controls: user-based access controls insufficiently limit privileges; Rule-based sandboxes; System call interposition; Integrity level access controls |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Rule-based controls: Fine grained: AppArmor |
| Software Security (SS) | Mitigating Exploitation | limiting privileges |